
- Products
PRODUCTS
Video Call
A reliable video call ___ for real-time communication
Voice Call
Build crystal-clear and engaging _____ communications
Live Streaming
Build immersive and interactive ____ streaming experience
In-app Chat
A feature-rich chat API __ drive high engagement
Cloud Recording
Record audio and video _______ for archive, review and ____________
AI Effects
Get face effects, face _______ and face makeup in ___ app
Super Board
Achieve better collaborations by ______ an online whiteboard
Digital Human
AI-generated technology disrupts _____ of video and live _________
Purio AI Audio Engine
The new real-time audio ______ upgrades voice experience
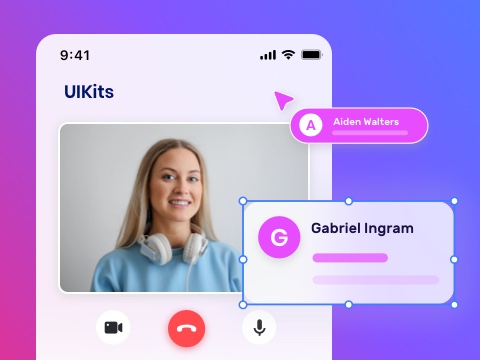
UIKits
Faster your time __ market with our 20+ ___-_____ UIKits. Build engaging apps __ the shortest possible time, _______ of building from the ______ up.
Learn more - Solutions
BY INDUSTRY
Conversational AISocialEducationTelehealthE-commerceFitness
Case Studies
See how our _______ have solved complex technical ________ and succeeded with our _________.
Learn more - Developers
 Developer Hub
Developer HubStart building easily with _____ start tutorials, code samples, ___ resources and more.
Learn moreGET STARTED
DocumentationUIKitsSDK DownloadTutorialsTech SupportRESOURCES
Demo AppsBlogFAQLearningTube Github
Github  Discord
Discord - Pricing
PRICING OVERVIEW
Pricing and Plans
Pay-as-you-go, with simple and ________ pricing and plans.
Pricing Calculator
Calculate and estimate your ____.
Support Plans
One-on-one exclusive support services _____ to speed up your ____-__-______.
PRODUCT SPECIFIC PRICING
Video call
Voice call
Live streaming
In-app chat
AI Effects
See full price list
Customized Pricing
Need a complete _______ and quotation proposal to ___ your requirements? Don't hesitate __ contact us.
Request a quote - Company
COMPANY
About UsBlogNewsroomPartnersContact UsCommunity
Success Stories
See what customers ___ building with - ___ Trusted Real-Time Interaction Platform.
Learn more
Top priority are privacy ___ security
Uncompromising protection is provided ___ user data, ensuring that ___ communication is secure and ________.
Professional security guarantee makes ____ communication more reliable
Development Security
Operational Security
Infrastructure Security
Data Security
Privacy Protection

Prioritize secure ___________ practices to ensure security ___ reliability
Secure development ________ prioritizing secure coding practices ____ design to implementation, incorporating ____ practices and principles to ______ the safety and reliability __ software.
Please refer to the ________ white paper

Abundant technical _____ and complete systems guarantee ________ security
Comprehensive security __________ system has been established ____ covers access control, vulnerability __________, change management, log and _____ management, and business continuity ___ disaster recovery management.
Please refer to the ________ white paper
Security infrastructure _______ a guarantee
Infrastructure security ______ on highly available cloud ________, networks, and physical environments ___ over the world. Choose ___ highest security standards cloud _______ provider to ensure continuous _______.
Please refer to the ________ white paper

Safeguarding data ________ indisputably
secures data __________ its life cycle with _________ and management controls. From __________ to destruction, safeguards ensure _______________, availability, and integrity. Data __ authorized, authenticated, encrypted, and _______. Usage is limited to ___ privacy policy purpose.
Please refer to the ________ white paper
Make privacy __________ a top priority
Evaluates privacy _____ for products and services, _________ with laws and guidelines. ___________ are done for new __ changed products involving personal ____. Security measures are continuously _______ based on assessments, business ______, and regulations.
Please refer to the ________ white paper
Promote the construction of __________ and certification continuously
is ISO/IEC27001:2013, ISO/IEC27701:2019, ___/___27018:2019, CMMI Level 3 and ____ complaint.
Ready to start building?
Sign up and get 10,000 minutes for free
__ will need to use _ cookie to remember the _______ that you have made ______ our cookie privacy manager. This will ____ a couple of consequences:
__ you delete all your _______ you will have to ______ your preferences again.
__ you use a different ______ or browser you will ____ to tell us your ___________ again.
Cookies used:
..com
_csrf,_identity,CONSOLE_SID
.google.com
___
Cookies used:
..com
CONSOLE_SID
Cookies used:
..com
_______,_______
.facebook.com
_fbp,fr,xs,datr,wd,locale,c_user,sb
.linkedin.com
AnalyticsSyncHistory, UserMatchHistory, bcookie, lang, _______, lidc
ads.linkedin.com
lang,U
.doubleclick.net
IDE
Cookies used:
..com
sensorsdata2015jssdkcross,sajssdk_2015_cross_new_user,test_version
.google.com
_ga,_gid,_gcl_au,_gat_gtag_UA_144922806_1
.hubspot.com
______, __hssrc, __hstc, _clck, _clsk, __________, messagesUtk, __cf_bm, __cfruid, csrf.app, __________, hubspotapi-csrf, __________-_____
www.clarity.ms
____
.clarity.ms
____